After going through various portals we came with Zero Trust security model article. Which will answer most of your queries like What is Zero Trust?, Architecture, benefits and some Statistics & Facts of zero trust.
What is a Zero Trust?
In order to gain or maintain access to applications and data, users must first be verified, authorized, and continuously checked for security configuration and posture, whether they are inside or outside the organization’s network. This security framework is known as “Zero Trust.” According to the Zero Trust model, there is no such thing as a traditional network edge. Instead, networks can be local, cloud-based, hybrid, or both, with employees and resources available anywhere.
In other words, Zero Trust is a security framework that mandates that before granting or maintaining access to applications and data, all users—whether inside or outside the organization’s network—must first authenticate, authorize, and undergo ongoing security configuration and posture validation.
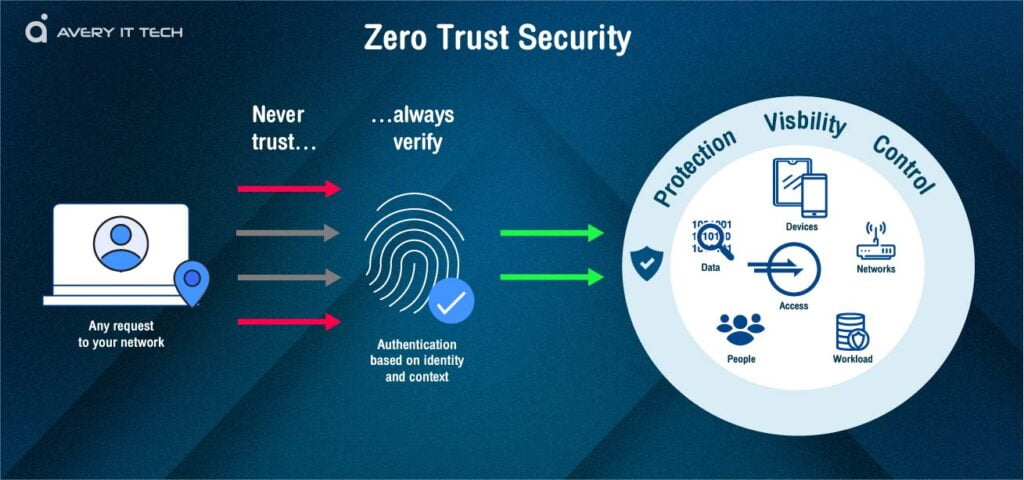
Image Source: averyittech.com
Zero Trust Architecture
Since John Kindervag, then at Forrester Research, popularized the phrase, a zero trust architecture has operated under the principle “never trust, always verify.” In order to prevent unauthorized access and lateral movement around an environment, a zero trust architecture enforces access regulations based on context, including the user’s role and location, their device, and the data they are requesting.
Establishing a zero trust architecture calls for strong multifactor authentication (MFA) methods beyond passwords, such as biometrics or one-time codes, as well as visibility and control over the environment’s users and traffic, including encrypted traffic, as well as monitoring and verification of traffic between parts of the environment.
Zero trust is being misused as a marketing term. Vendors are applying the term ‘Zero Trust’ to market everything in security, creating significant marketing confusion.
Gartner, 2019
The Advantages of Zero Trust Architecture
Cybercriminals seeking to steal, destroy, or demand ransom for business-critical and sensitive data, including personally identifiable information (PII), intellectual property (IP), and financial information, may find today’s cloud systems to be alluring targets.
Zero trust is one of the most effective security measures available today, despite the fact that no security measure is flawless and data breaches can never be entirely eradicated. Zero trust lessens the attack surface and lessens the effect and severity of cyberattacks, which cuts down on the amount of time and money needed to respond to breaches and to clean them up.
Not to mention that the best method for cloud security currently available is a zero trust security paradigm. Given the amount of cloud, endpoint, and data sprawl in today’s IT settings, the capacity to not trust any connection without adequate verification is crucial. Plus, the increase in visibility will make life much easier for IT and security from the administrator level all the way up to the CISO.
How Does Zero Trust Security Work?
Zero trust’s main principle is straightforward: by default, consider everything hostile. It represents a significant shift from the network security architecture, in use since the 1990s, that is based on a centralised data centre and a secure network perimeter. These network architectures rely on approved IP addresses, ports, and protocols to set up access controls and verify what is trusted inside the network, which typically includes anyone joining via a remote access VPN.
A zero trust strategy, in contrast, views all traffic as hostile even if it is already inside the perimeter. Workloads may be prevented from communicating, for instance, until a set of qualities, such as a fingerprint or identity, has verified their validity.
Zero Trust Principles
Zero trust goes beyond user identification, audience targeting, and protected access. It is a method for creating a cybersecurity ecosystem. Three principles form the basis of it:
- Close all connections: “Passthrough” technologies, such as firewalls, examine files as they are transmitted. Alerts are frequently delivered too late if a malicious file is found. In order to enable an inline proxy architecture to analyse all traffic, including encrypted information, in real time—before it reaches its destination—and thwart ransomware, malware, and other threats, a successful zero trust solution terminates every connection.
- Protect data with context-based policies that are specific and granular: Zero trust policies check access requests and privileges depending on context, such as user identification, device, location, type of material, and the application being requested. User access privileges can change based on policies.
- Eliminate the attack surface to reduce risk:
Users never connect to networks using a zero trust strategy; instead, they connect directly to the apps and services they require (see ZTNA). Direct connections between users and apps reduce the possibility of lateral movement and stop compromised devices from infecting other resources. Additionally, users and apps cannot be found or attacked since they are invisible to the internet.
Zero Trust – Statistics & Facts
1. In 2021, ZT security initiatives among companies stood at 90 percent, up from just 16 percent in 2019. By 2027, the global Zero Trust market is expected to be worth nearly 60 billion U.S. dollars.
2. As of January 2022, most companies worldwide already had a formal ZT strategy in execution, driven by the need to enable secure remote access for their employees, and modernize their cyber security infrastructure.
3. From a national perspective, in 2021, the U.S. was the country reporting a fully implemented a ZT strategy, as opposed to Germany.
4. In 2021, the global Zero Trust security market amounted to nearly 23 billion U.S. dollars and was forecast to increase to almost 60 billion U.S. dollars by 2027.
5. 72% of organizations around the world have either adopted Zero Trust or are in the process of planning or adopting it.
Data Sources: Microsoft, statista, zscaler, redhat
Article by
Skillshouter Team
